- Published on
How to Limit AWS IAM User Access to a Single S3 Bucket
One of the common security practices is the principle of least privilege concept which is basically as a user you ONLY have permission to do your job, nothing more nothing less. (And, please avoid using admin access unless you're aware of what you're doing)
For example, if you're building a SaaS and plan on using AWS S3 for file storage. Then your app should have access only to the AWS S3 bucket for your app and it should not be able to access anything else from your AWS account.
For such cases, we can use AWS IAM to restrict the security.
In this blog post, let's see how to create an AWS IAM user who has access to only one AWS S3 bucket (nesinio-example). And I've added step by step screenshot for your reference (as you know AWS UI is not that user-friendly)
Let's get started
Create IAM User & Policy
Once you've logged in to the AWS console head over to AWS IAM and create a new user. It's a 3-step wizard
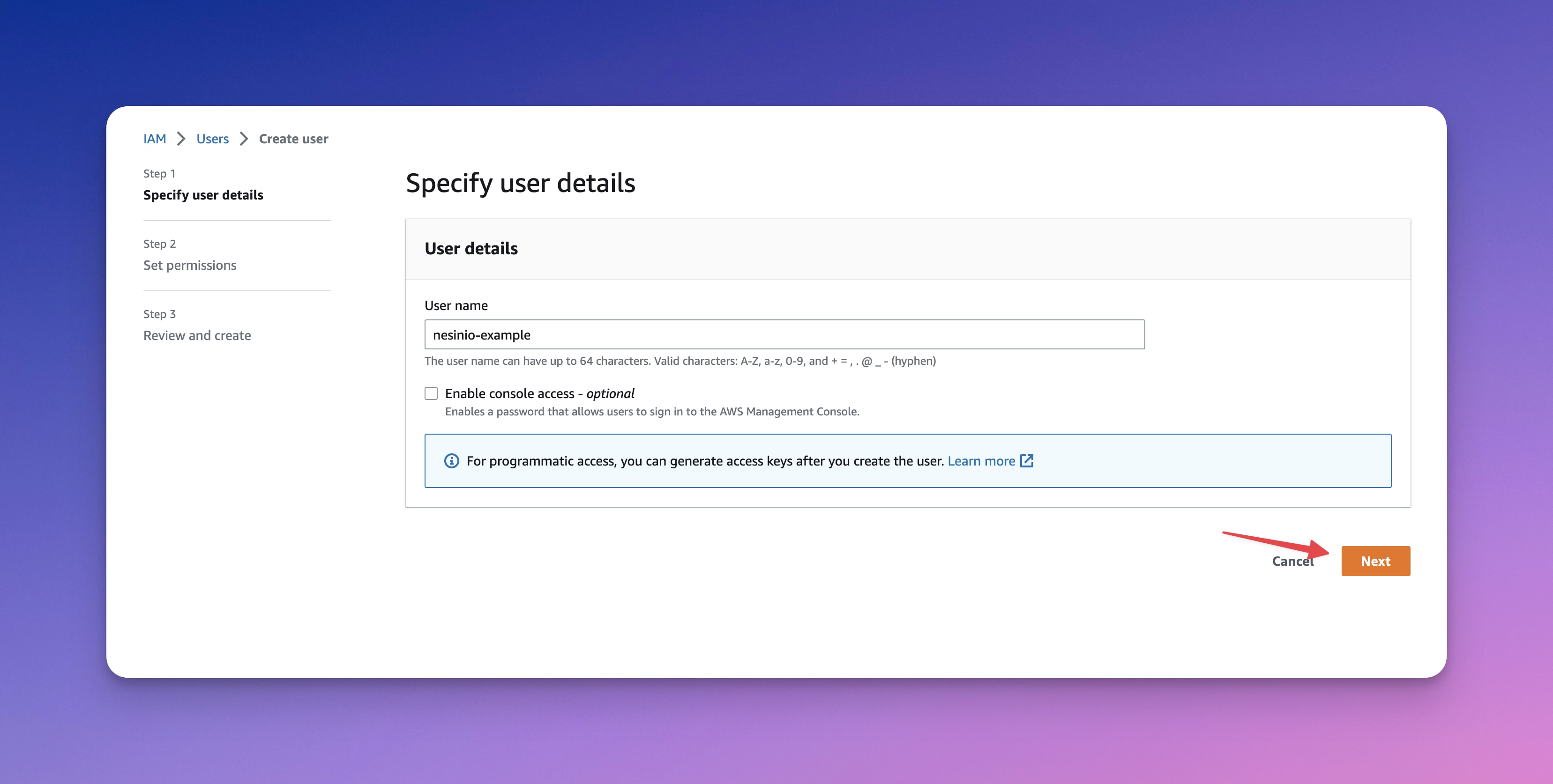
Step #1: Username
In this step enter your IAM user name and click on Next
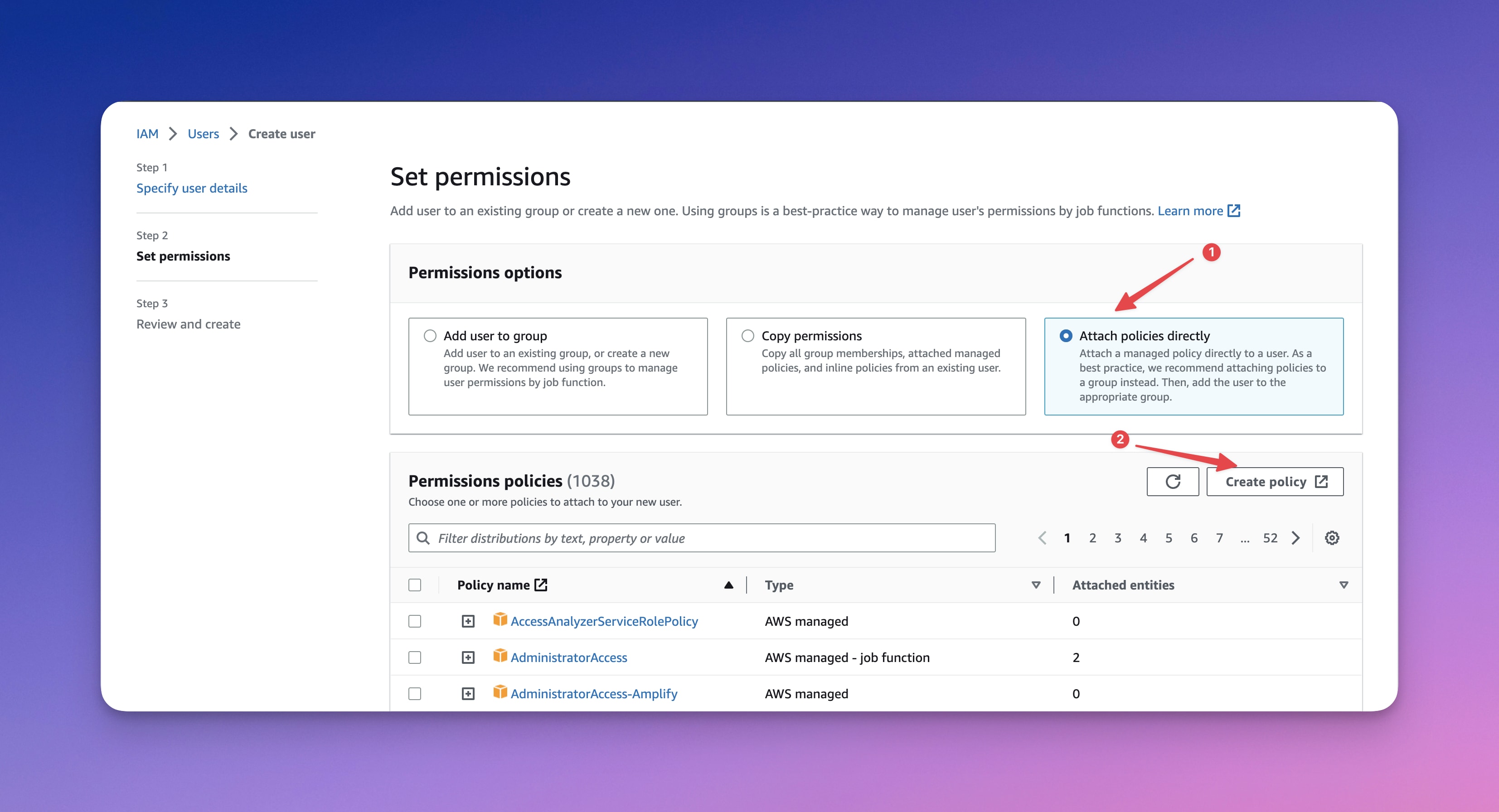
Step #2: Create a new policy & attach
In this step, you'll need to create a new policy in which we'll give access to a single AWS S3 bucket (nesinio-example) and then directly attach the policy to the user
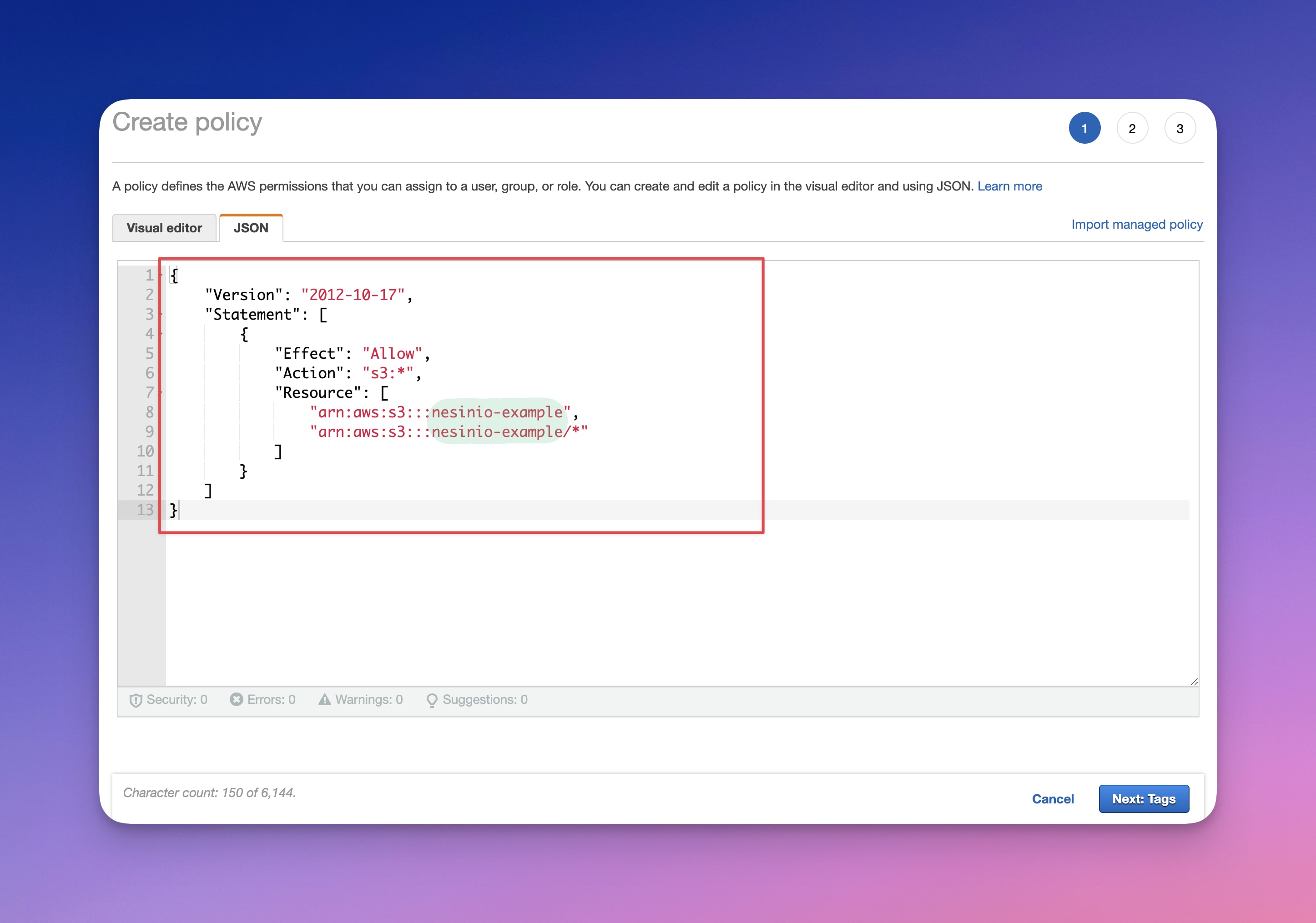
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "s3:*",
"Resource": [
"arn:aws:s3:::nesinio-example",
"arn:aws:s3:::nesinio-example/*"
]
}
]
}
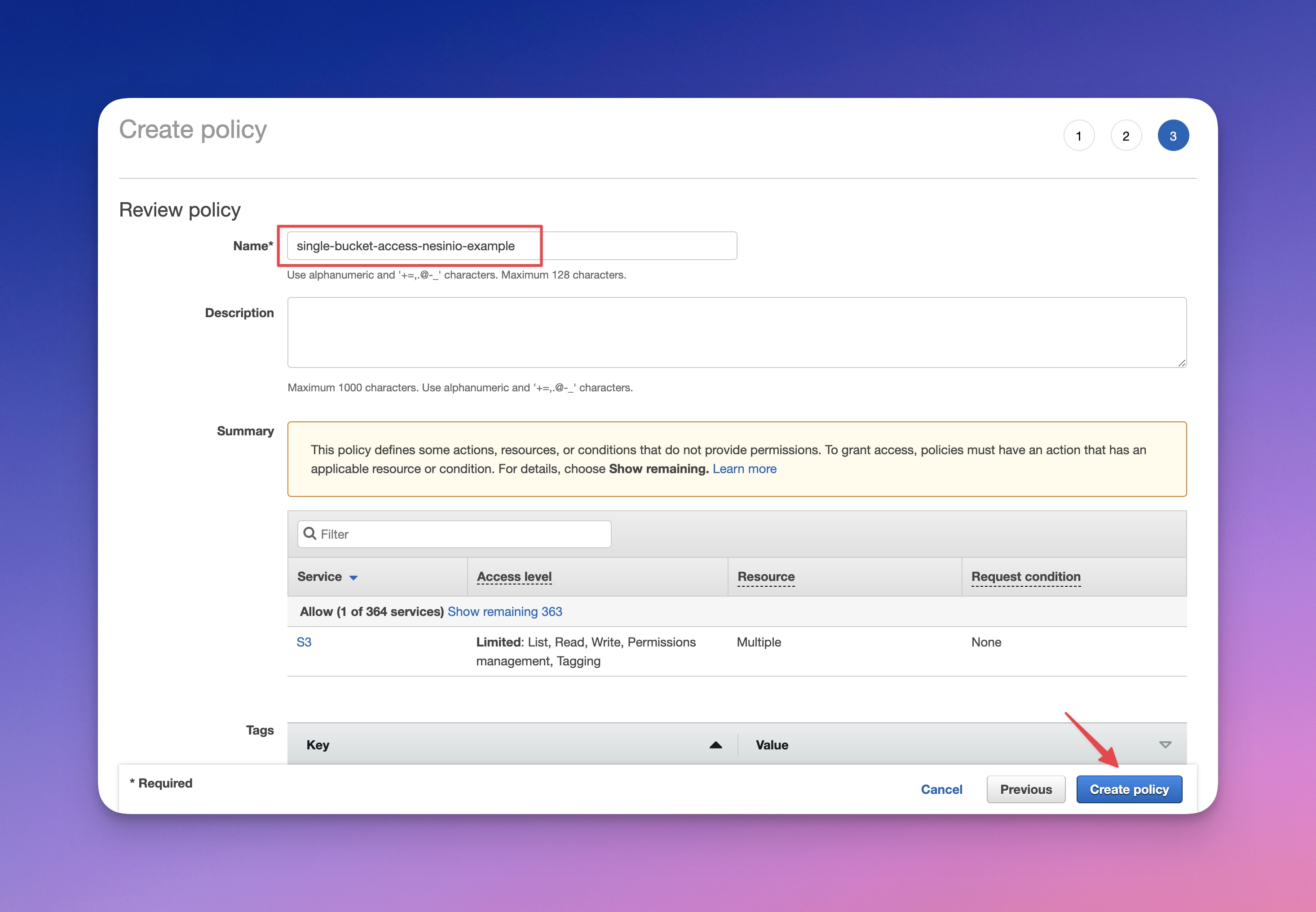


And now, we've created a new IAM user with access to a single AWS S3 bucket.
Generating Access key for IAM User

Once the IAM user is created, we'll need to get access keys to perform operations like uploading/downloading/anything else with AWS S3 using SDK.
Here is how to do it:
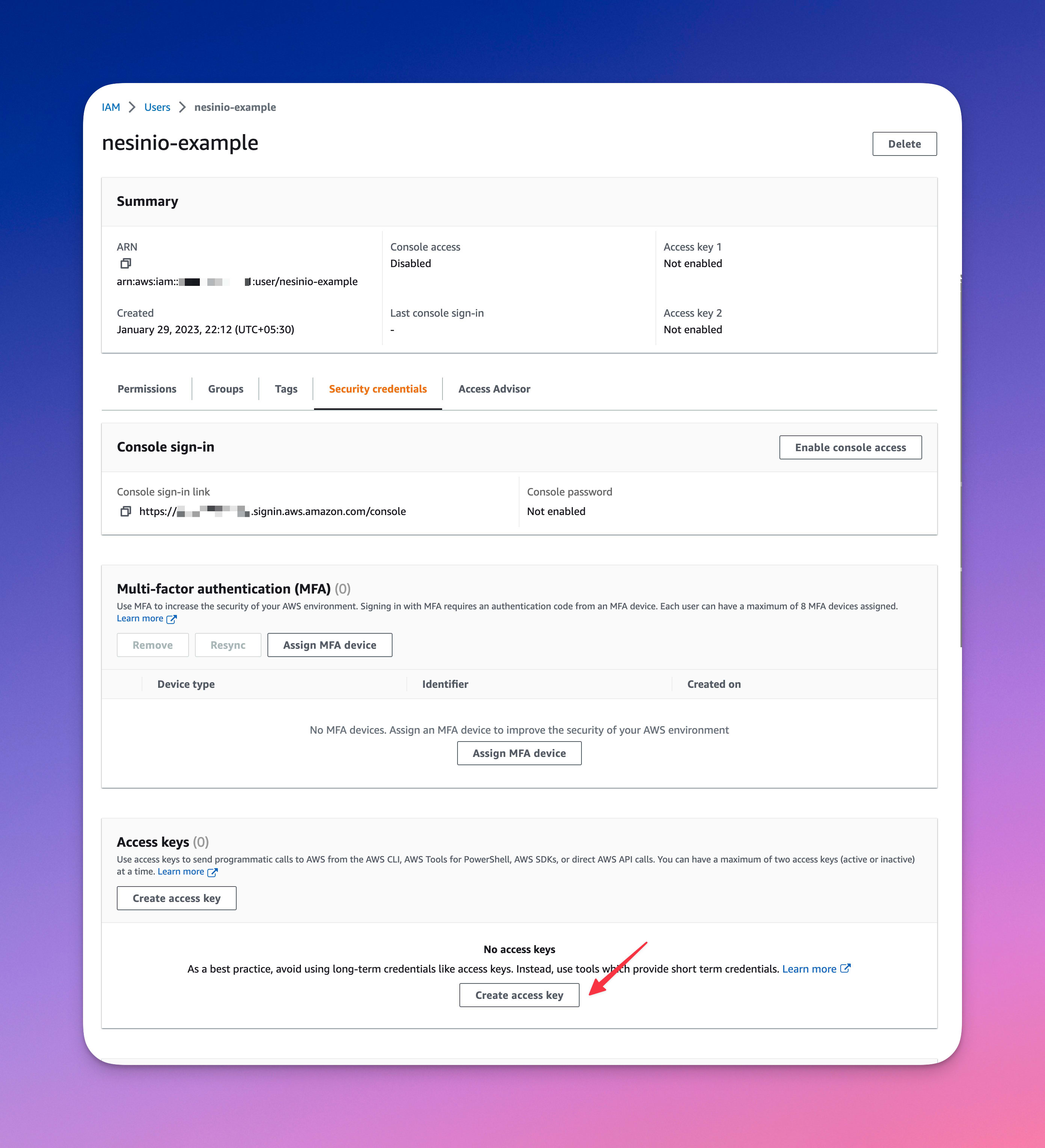


That's it. Your access key will have access to ONLY one AWS S3 bucket 😇
Happy secure S3!